Capturing HTTPS Traffic
Fluxzy intercepts HTTPS traffic by acting as a man-in-the-middle proxy, decrypting SSL/TLS connections for inspection and debugging. This guide covers three capture methods:
- System proxy – Capture all OS-wide traffic
- Source filtering – Capture only specific hosts or applications
- Captured browsers/terminals – Launch isolated instances with pre-configured proxy settings
Prerequisites: Ensure the Fluxzy root certificate is installed to avoid SSL errors when intercepting HTTPS traffic.
Proxy Status
At startup, Fluxzy automatically starts the proxy and listens on localhost. The bound addresses are displayed in the status panel.
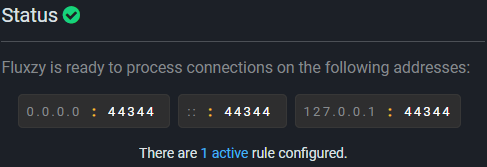
The proxy status indicator in the bottom-right corner shows the current state:

Any client manually configured to use the proxy endpoint will have its traffic captured automatically.
Capturing OS Traffic
Capture All Traffic
To intercept all system-wide traffic, click the Capture button in the toolbar, or use the menu: Capture > Start Recording.
When enabled, Fluxzy registers itself as the system proxy. All HTTP/HTTPS traffic from applications that respect system proxy settings will be captured.

Capture Specific Traffic with Source Filtering
For targeted capture, use source filtering to intercept only traffic matching specific criteria (e.g., specific hosts, ports, or applications). Only filters with OnAuthorityReceived scope are eligible for source filtering.
To configure a source filter:
Click the filter icon in the toolbar

Select your filter criteria from the dialog
When active, the filter icon turns yellow

Note: When source filtering is enabled, non-matching traffic still passes through the proxy but is tunneled directly to its destination without interception or recording. To completely bypass the proxy for certain hosts, add them to the bypass list: Settings > Proxy Settings > Bypass List.
Capturing Browsers and Terminals
Fluxzy can launch captured instances of browsers and terminals installed on your system. This approach is useful when you want to:
- Avoid noise from background OS traffic
- Test a specific browser without affecting your main browsing session
- Debug CLI tools or scripts in an isolated environment
To launch a captured application:
Go to Capture > Launch Captured Application
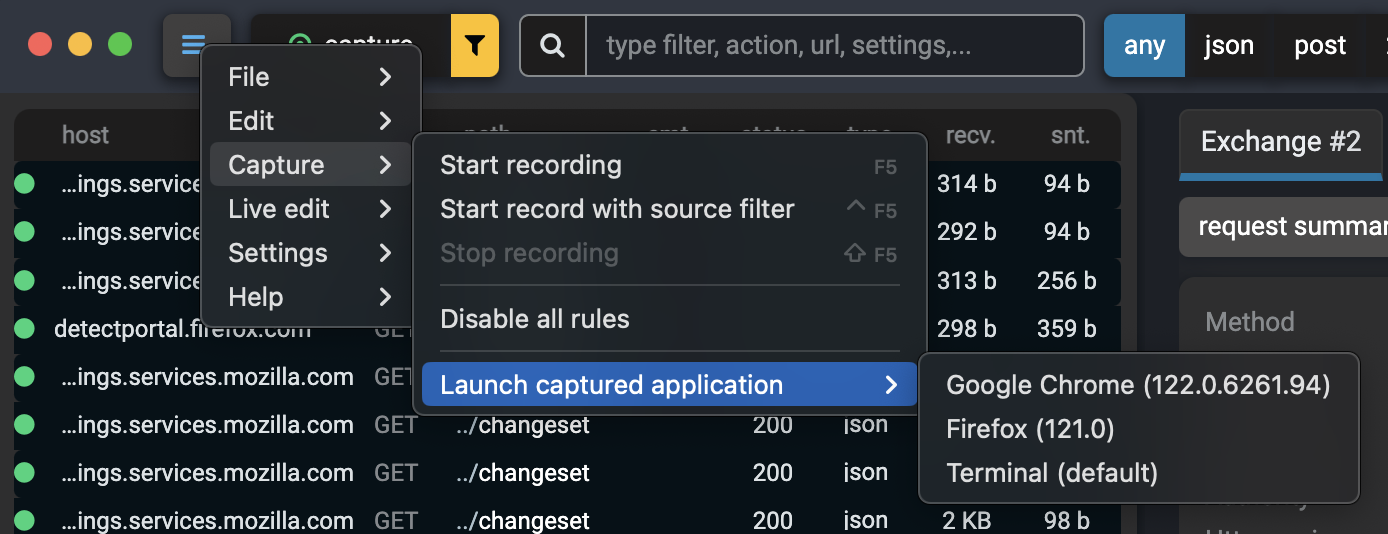
Select the browser or terminal you want to launch
The launched application is pre-configured to route all traffic through Fluxzy. No additional proxy configuration is needed.

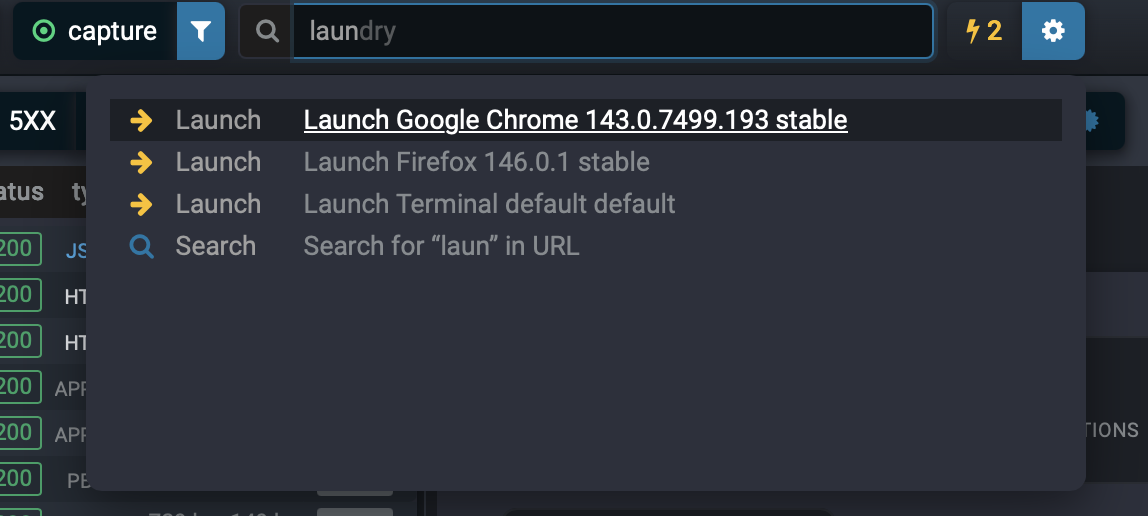
Quick Launch with Search
Captured applications are also accessible via the Search Everywhere feature (press Ctrl+K or Cmd+K):
Troubleshooting
Port Already in Use
If the default port (44344) is occupied by another application, an error appears in the status panel:
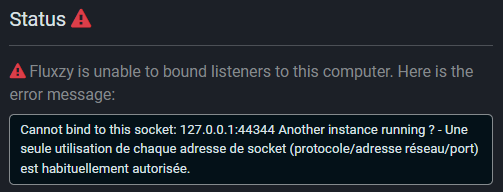
Solutions:
- Close the application using the port, then restart Fluxzy
- Change the proxy port: Settings > Proxy Settings > Port
No Traffic Being Captured
If traffic isn't appearing in Fluxzy:
- Verify proxy is running – Check the status indicator in the bottom-right corner (should be green)
- Check application proxy support – Some applications ignore system proxy settings (use captured browsers instead)
- Verify certificate installation – HTTPS traffic requires the root certificate to be trusted
- Check bypass list – Ensure the target host isn't in the bypass list
SSL/Certificate Errors in Captured Traffic
If you see certificate warnings or SSL errors:
- Verify the Fluxzy root certificate is installed: Settings > Certificates > View CA Certificate
- Ensure the certificate is trusted in your OS certificate store
- For specific applications, you may need to configure certificate trust separately
Next Steps
- Install the root certificate for HTTPS interception
- Filter and search captured traffic to find specific requests
- Create rules to modify traffic on the fly
- Export captured sessions for sharing or analysis