Configure PCAP capture
Fluxzy has the capability to decrypt HTTP exchanges and capture raw network packets in the PCAPNG format.
For each HTTP exchange, Fluxzy can extract the captured pcap of the underlying connection without any additional configuration.
By default, the file format (.fxzy) combines captured raw packets within decrypted HTTP exchanges, providing quick access to packet sequences that correspond to a specific HTTP exchange.
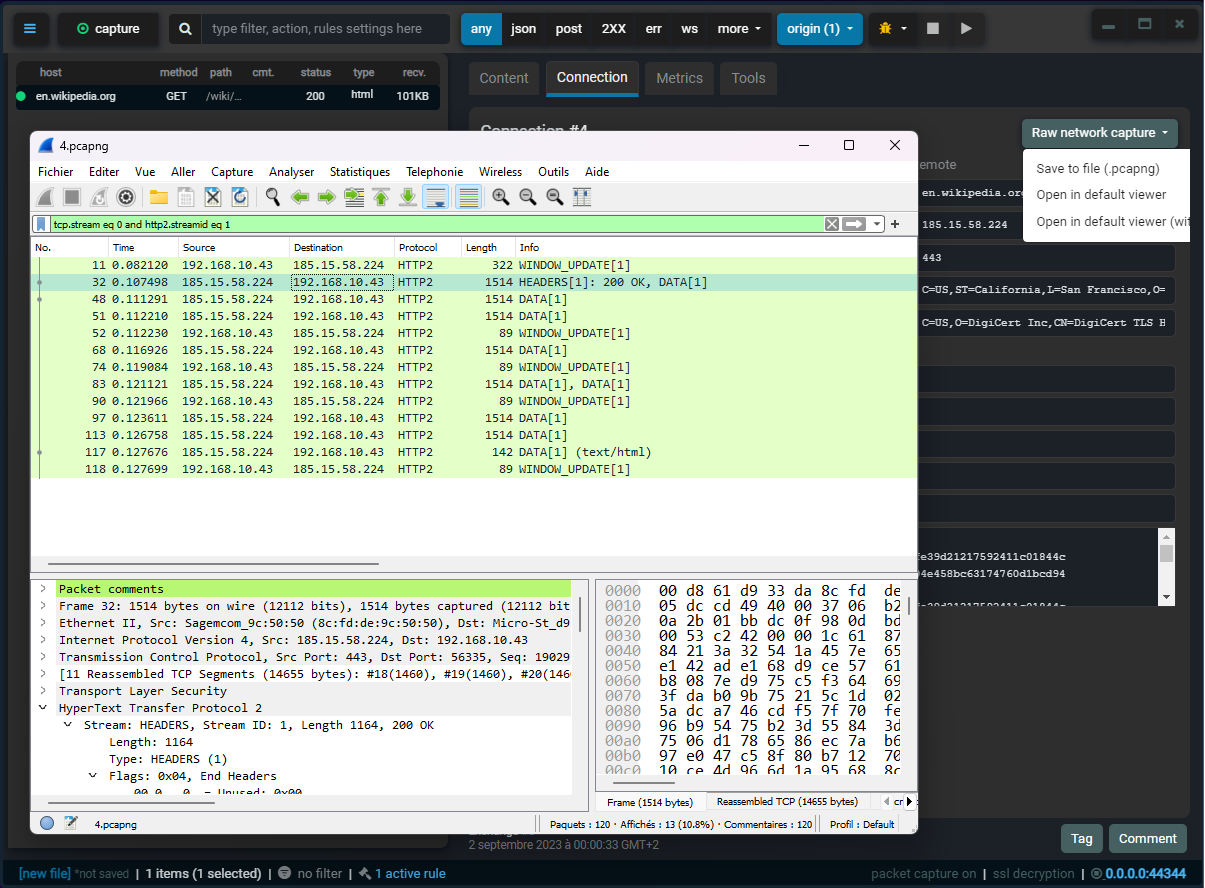
The raw capture above is displayed using Wireshark.
Prerequisites
Fluxzy does not come with a built-in capture engine. However, it can connect to any compatible existing capture engine that supports the pcap interface.
On Linux
Install libpcap or any equivalent capture library.
On a debian based distribution, you can run:
sudo apt-get install libpcap-dev
On macOS
libcap is installed perdefault on macOS starting Catalina. If the package is missing, you can install it with homebrew.
brew install libpcap
Additionaly, if you can install the wireshark-chmodbpf to allow packet capture without having to elevate the application.
bashbrew install --cask wireshark-chmodbpf
On windows
Install WinPcap or any equivalent capture library. Fluxzy will automatically bind to the capture library to collect the raw packets.
With docker
No additional installation is required. Libpcap is already embedded in the container.
Enabling raw capture
Fluxzy Cli (fxzy)
The -c or --include-dump option enables raw packet capture within the fxzy start command group.
fxzy start -sp -c -o /tmp/capture.fxzy
The above command initiates a capture session with raw packets and saves the results in /tmp/capture.fxzy.
Note:
the -sp option make Fluxzy act as a global proxy for the running OS.
Fluxzy Desktop
Activate option Settings > Raw capture > Enable raw capture to enable raw capture with the desktop application. For macOS and linux, you need to activate the option Run external process to capture raw packets in order to not having to elevate the whole application.
When network capture is activated, a specific button (Raw network capture) is available under the Connection tab.
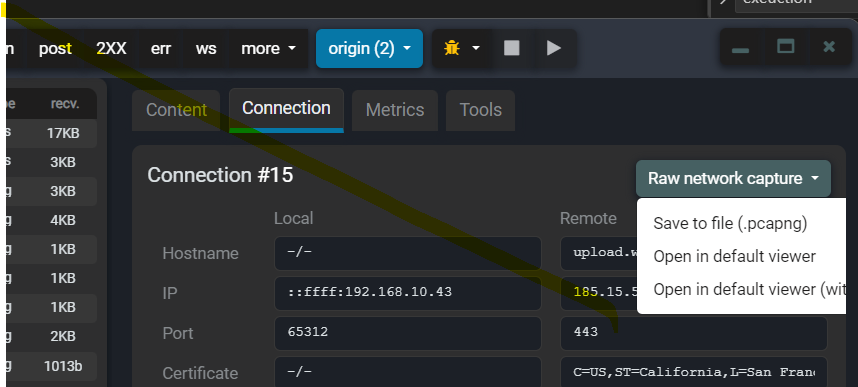
Capturing NSS Key logs
NSS Key logs are ephemeral keys exchanged between a client and server during a SSL/TLS session. These keys provides the necessary information for decrypting the SSL/TLS session.
Fluxzy can capture NSS Key logs along with the raw packets. However, to enable this feature, the Bouncy Castle SSL engine must be used.
This engine can be activated from Fluxzy CLI through the option: --bouncy-castle or in Setting -> SSL Settings -> Use
Bouncy Castle for Fluxzy Desktop.
Fluxzy will incorporate these NSS Key logs into the PCAPNG file, allowing immediate decryption and viewing using tools like Wireshark, without requiring any additional configuration.
Fluxzy supports the environment variable SSLKEYLOGFILE to specify the location of the NSS Key logs file.