Comprehensive Rules
Rewrite reality. 50+ actions, mock responses, spoof DNS, throttle bandwidth, fake auth. Edit visually or dive into YAML.
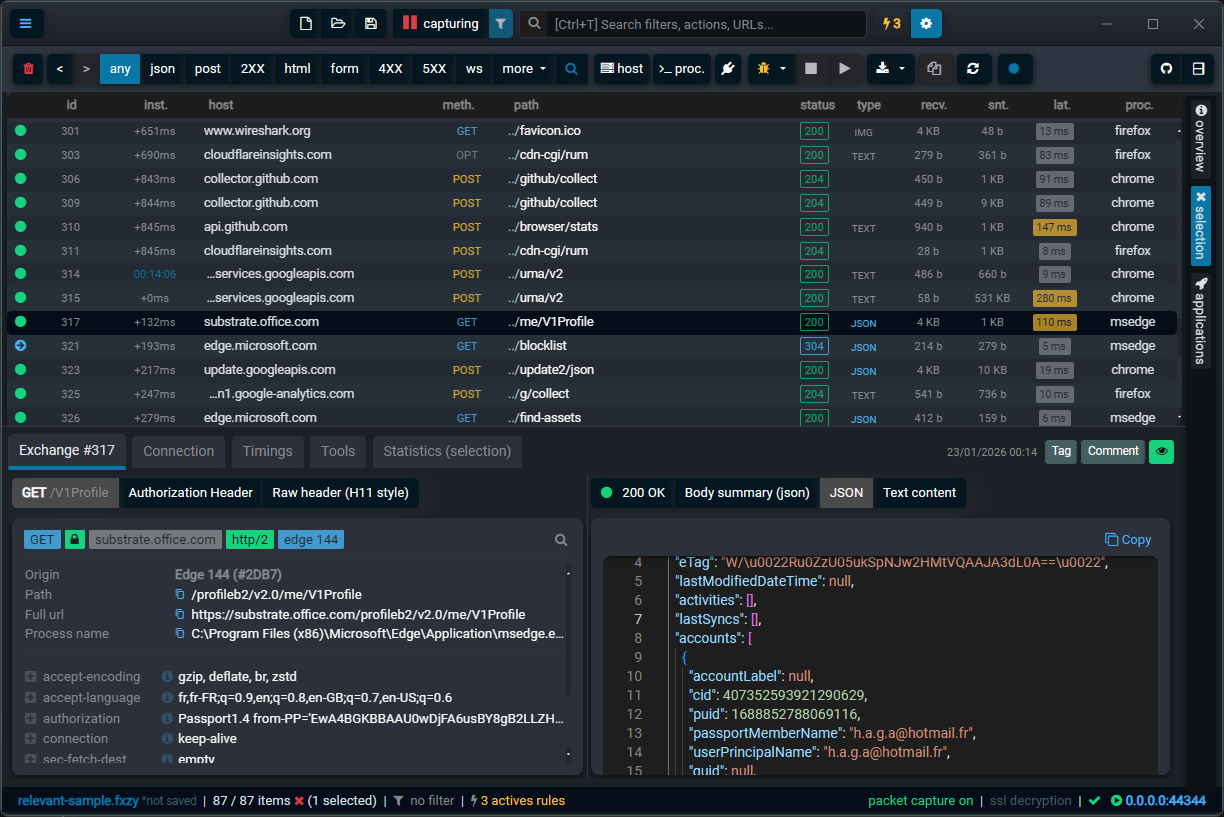
Fluxzy intercepts traffic at the protocol level — HTTP/1.1, HTTP/2, WebSocket — with full header inspection, body decoding, and timing analysis. Forensic-grade capture for production-grade debugging.
Rewrite reality. 50+ actions, mock responses, spoof DNS, throttle bandwidth, fake auth. Edit visually or dive into YAML.
Skip the system proxy dance. Launch Chrome, Firefox, or any app directly, already hooked and ready to intercept. Zero config.
Pause traffic at any stage, DNS lookup, before request, after headers. Step through the network like stepping through code.
One click, and Fluxzy becomes your system proxy. Every HTTP request from every app flows through, no manual browser config needed.
PCAP recording is live. Every packet gets saved, not just HTTP, the whole conversation. Wireshark-ready, no extra tools.
Ctrl+T your way through Fluxzy. Jump to filters, rules, settings, exchanges, anything. Type what you need and you're there.
Find anything, fast. Ctrl+click to stack filters with AND, Shift+click for OR. Ctrl+Shift live debugs the next matching request. Create and save filter.
Full Monaco editor for your response body. Syntax highlighting, code folding, search, the same editor powering VS Code.
Select two exchanges, hit diff. Headers, body, cookies—everything side by side, changes highlighted. Find what broke between "it worked yesterday" and "it's broken now" in seconds.

Built with an open-source HTTP engine for maximum transparency and extensibility
Captures everything from PCAPNG with SSLKEYLOG to deciphered HTTP1.1/H2/Websocket exchanges.
Runs on Windows, macOS, linux and collects traffic for any remote devices including iOS and Android.
Halt, edit, resubmit, replay, mock, redirect, spoof, ... Fluxzy has everything you expect from an HTTP debugger.
Fast throughput, always streaming by design, every processing block of fluxzy engine has been created to produce minimal overhead.
Express simple and declarative directives with YAML files and let Fluxzy connect them to the 100+ built-in filters, actions, and rules.
Deflect OS trafic directly to fluxzy or run and hook existing browsers and terminals. Supported environments are Windows, macOS and Gnome based application.
A modern and intuitive HTTP debugger to enhance your debugging workflow




Get a complete and unlimited version of Fluxzy Desktop Community Edition — free forever, no credit card required.
Download FreeShape web streams in a simple, straightforward, and declarative way
rules:
- filter:
typeKind: AnyFilter
action :
typeKind: UpdateRequestHeaderAction
headerName: user-agent
# previous reference the original value of the user-agent header
headerValue: "{{previous}} - Relayed by fluxzy"fluxzy start -r update-user-agent.yaml
rules:
- filter:
typeKind: HostFilter
pattern: google.com
operation: endsWith
action :
# This action remove any cache directive from request and response header
typeKind: RemoveCacheActionfluxzy start -r remove-cache-command.yaml
rules:
- filter:
typeKind: HostFilter
pattern: google.com
operation: endsWith
actions:
# Add a comment to any exchange to google.com
- typeKind: ApplyCommentAction
comment: Hello fluxzyfluxzy start -r set-comment-command.yaml
rules:
- filter:
typeKind: HostFilter
pattern: mtls.domain.com
- action:
typeKind: SetClientCertificateAction
clientCertificate:
pkcs12File: certificate.pfx
# password is taken from environment variable CERT_PASSWORD
pkcs12Password: ${env.CERT_PASSWORD}
retrieveMode: FromPkcs12fluxzy start -r client-certificate.yaml
rules:
- filter:
typeKind: FilterCollection # can be multiple combination of filters
operation: and
children:
- typeKind: postFilter # select only post requests
- typeKind: requestHeaderFilter
headerName: authorization # select only request with authorization header
operation: regex
pattern: "Bearer (?<BEARER_TOKEN>.*)" # A named regex instructs fluxzy
# to extract token from authorization
# header into the variable BEARER_TOKEN
action :
# Write the token on file
typeKind: FileAppendAction # Append the token to the file
filename: token-file.txt # save the token to token-file.txt
text: "${authority.host} --> ${user.BEARER_TOKEN}\r\n" # user.BEARER_TOKEN retrieves
# the previously captured variables
runScope: RequestHeaderReceivedFromClient # run the action when the request header
# is received from client
fluxzy start -r capture-bearer-token.yaml
Access all Fluxzy features — from request recording to advanced traffic alteration — in your own code with the open-source Fluxzy NuGet packages.
Download Fluxzy for free and start capturing, analyzing, and modifying HTTP traffic in minutes.
Download Now